Date updated: 21 July 2024 | by Sybil Mayard
Cybercrime is constantly on the rise, and therefore you must make cyber security a top priority for your business. Keep yourself, your business and your customers safe with the tips and advice in our blog.
By following good cyber security practices, you can enjoy a safe and secure experience both online and offline.
1. Don't Delay, Update Your Devices Today!
Install an antivirus product on your devices and keep it up to date. Carry out a virus scan regularly to detect and remove any malicious software.
Keep all of your devices' operating system software up to date. By default, devices are usually set to download and install the updates automatically. However, if this will be disruptive to your working day, add a recurring appointment to your calendar to remind yourself to manually install the updates at a more convenient time.
Only download apps and software from legitimate sources and always install the latest version.
2. Be Careful With Your Passwords
Do not reuse passwords across multiple websites!
Do not store passwords on spreadsheets, emails, hard drives, or on paper. Instead, use a password manager such as LastPass or Dashlane. Password managers are simple, secure and convenient to use. Both of these platforms include a free plan which allows you to store an unlimited number of passwords. Once you have stored all of your passwords in the password manager, go through your notes and emails, and delete any that contain passwords.
For each account, create a strong, unique password. A strong password is at least 16 characters long, consisting of a random combination of uppercase and lowercase letters, numbers and special characters (such as @, #, _, -, &, *, ^). For some interesting stats, download the famous Hive Systems Password Table which illustrates how long it takes for a hacker to brute force a password in 2024.
2-Factor Authentication
Where possible, set up 2-factor authentication, or 2FA (also known as two-step verification). This adds an extra layer of security to your account because the access requires 2 forms of identification (the password and a security code). Common forms of 2FA include SMS verification, which involves sending a text message to your phone containing a unique security code, or obtaining a code via an authentication app. As well as your password, you would need to enter this code into the website to gain access to your account. Never share your security code with others.
When setting up 2FA, you should also create a backup method to access your account if you lose your phone. This is usually in the format of a recovery code. Please store your recovery codes in a safe place such as in a password manager.
3. Manage Permissions Wisely
If your organisation hires employees or contractors, each user will need their own, separate login for each account. Logins should not be shared between users. Remember the "Principle of Least Privilege"; that is, don't automatically grant all users admin permissions. Instead, provide each user with the lowest level of access required to perform his or her job effectively and keep the number of users with admin permissions down to a minimum. Delete logins for users who no longer work for your organisation.
4. Protect Your Data and Others' Data
Lock the screen when away from your computer or laptop. If possible, enable the encryption feature on your laptop. BitLocker is available for Windows, and FileVault for Mac.
Do not store personal data for longer than it is needed.
Keep devices and documents stored safely and away from unauthorised personnel.
Keep all of your documents and data backed up. Create one backup in the cloud and at least one other backup on a physical hard drive stored in a location different from where you usually work. Back up your work frequently, ideally once a day.
Here are a few options for cloud backup solutions, all of which offer a free plan for a limited amount of storage space:
- Google Drive
- Dropbox
- IDrive
- MEGA
Responding to a Data Breach
Have an incident response procedure in place and in the event of an incident, record as much information as you can about it (what happened and when, why it happened, who was involved, what data was lost, which action you took etc.).
Remember: if your organisation suffers a data breach, and personal data is involved, you may need to report it to the Information Commissioner's Office (ICO) within 72 hours. When in doubt, please contact us and our experts will advise you on the best course of action.
5. Beware of Spam
If you get inundated with junk emails every day, it can be tempting to click the Unsubscribe link at the bottom of the emails. Never click this link or respond to the emails as this indicates to the spammers that your email address is active and could result in your receiving even more junk mail.
6. Learn How to Identify Scam Emails and Texts
Scam emails and texts often contain phrases like the following to lure you into taking action:
- Your account has been suspended
- We detected unusual activity on your account
- Someone tried to log in to your account
- Your password has expired
- You're eligible to receive a grant
- You're due to receive a tax refund
- Your package could not be delivered
Do not click links in suspicious emails or texts. These links can take you to a website that looks like a genuine site but isn't, in an attempt to steal your personal information.
Do not open attachments from suspicious emails. Attachments can contain viruses or other malware that can also steal your information or harm your computer.
Never respond to an email that promises a large amount of money in return for your personal information.
Look at the email address of the sender. If the domain (the part after the @ sign) doesn't match the company it appears to be coming from, then it's fake.
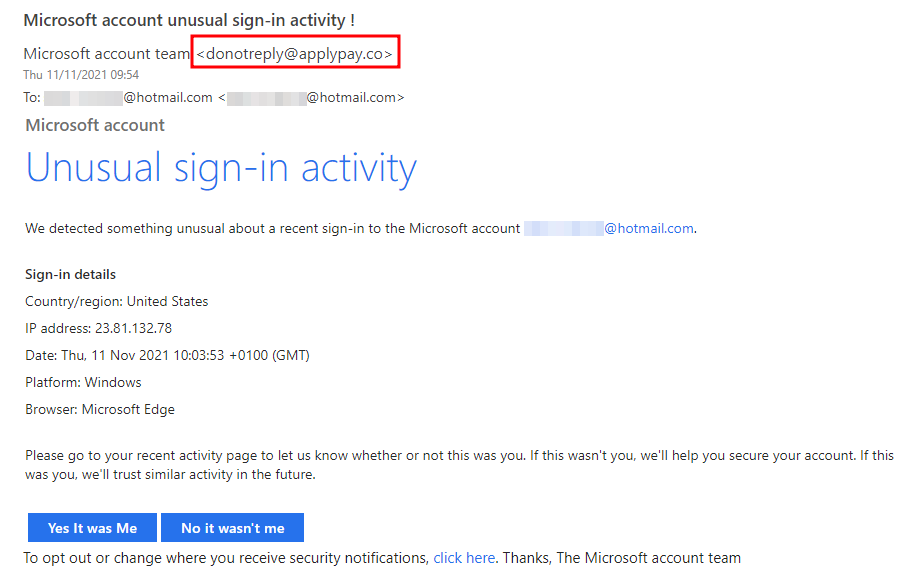
Read the email carefully and look for spelling, punctuation and grammar mistakes.
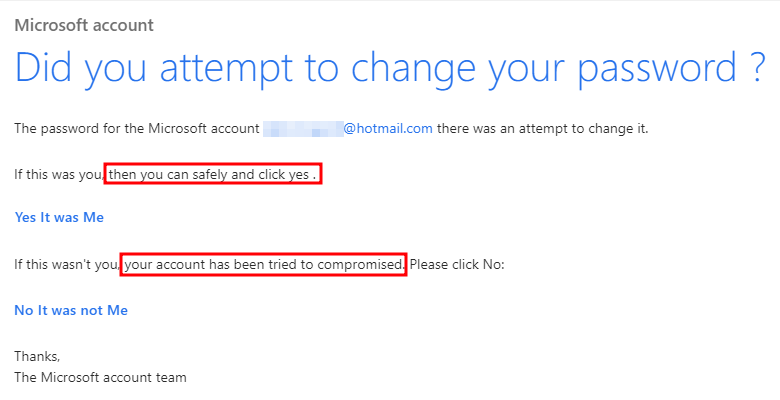
Look out for the generic "Dear customer" greeting.
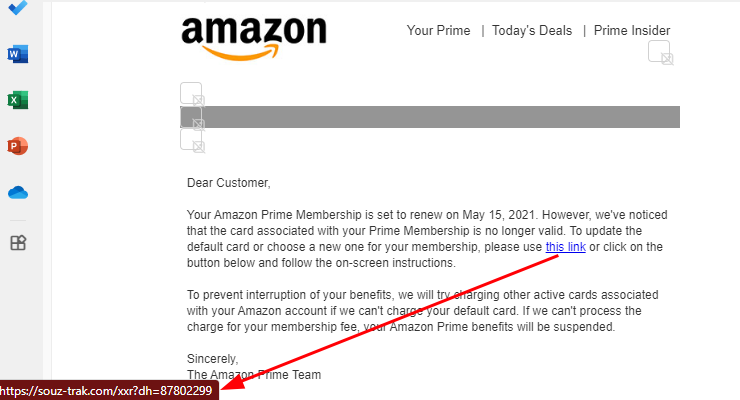
Learn how to spot deceptive links. Do not click on links; instead, hover over the links and buttons to check if the links are genuine:
If you receive a suspicious email, report it as Phishing via your email program and delete it immediately. You can also block the sender to avoid receiving further emails from this sender, however, this is usually ineffective as scammers constantly change their email addresses.
7. Practice Safe Browsing Online
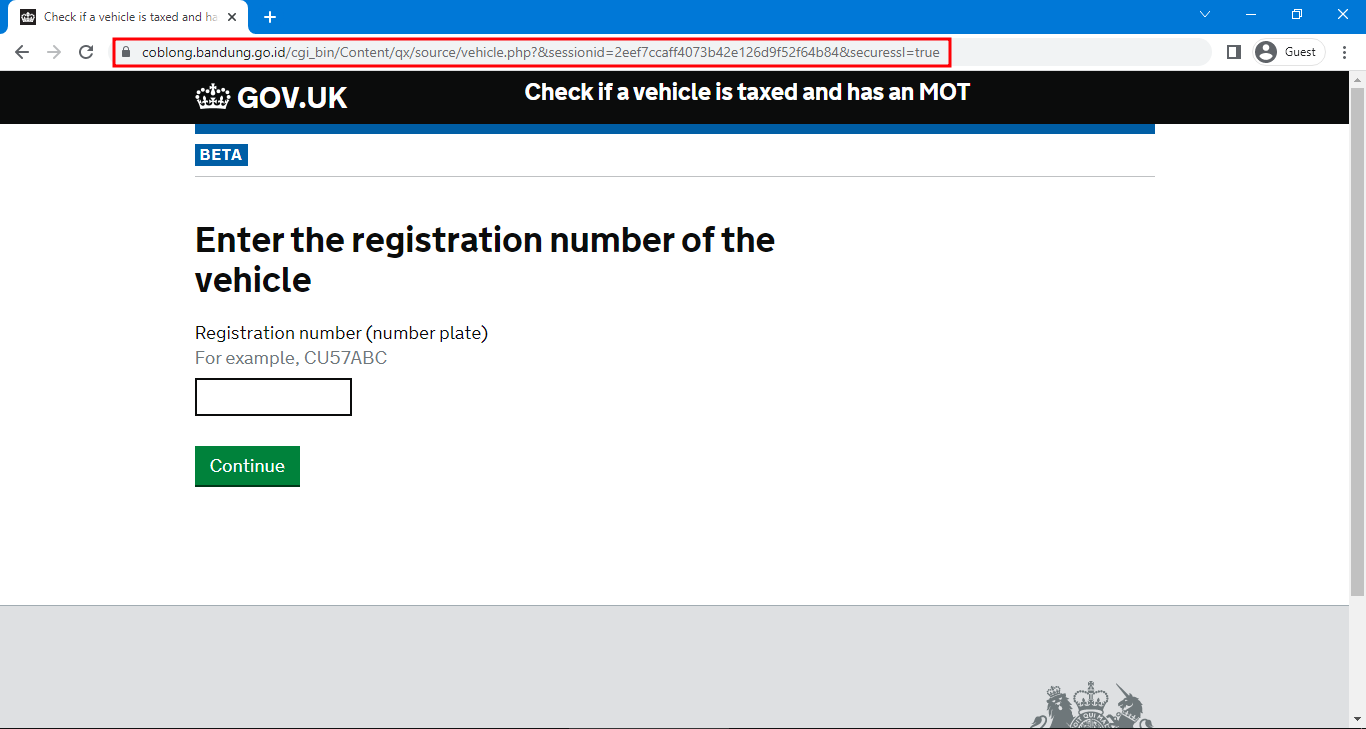
Check that the website you are viewing is actually the one you intended to visit - verify that the URL in the address bar of the browser is correct. Spoof sites can be deceptive and are designed to look identical to the real ones. Have a look at this example of the vehicle enquiry service on the GOV.UK website.
A fake GOV.UK website:
The genuine GOV.UK website:
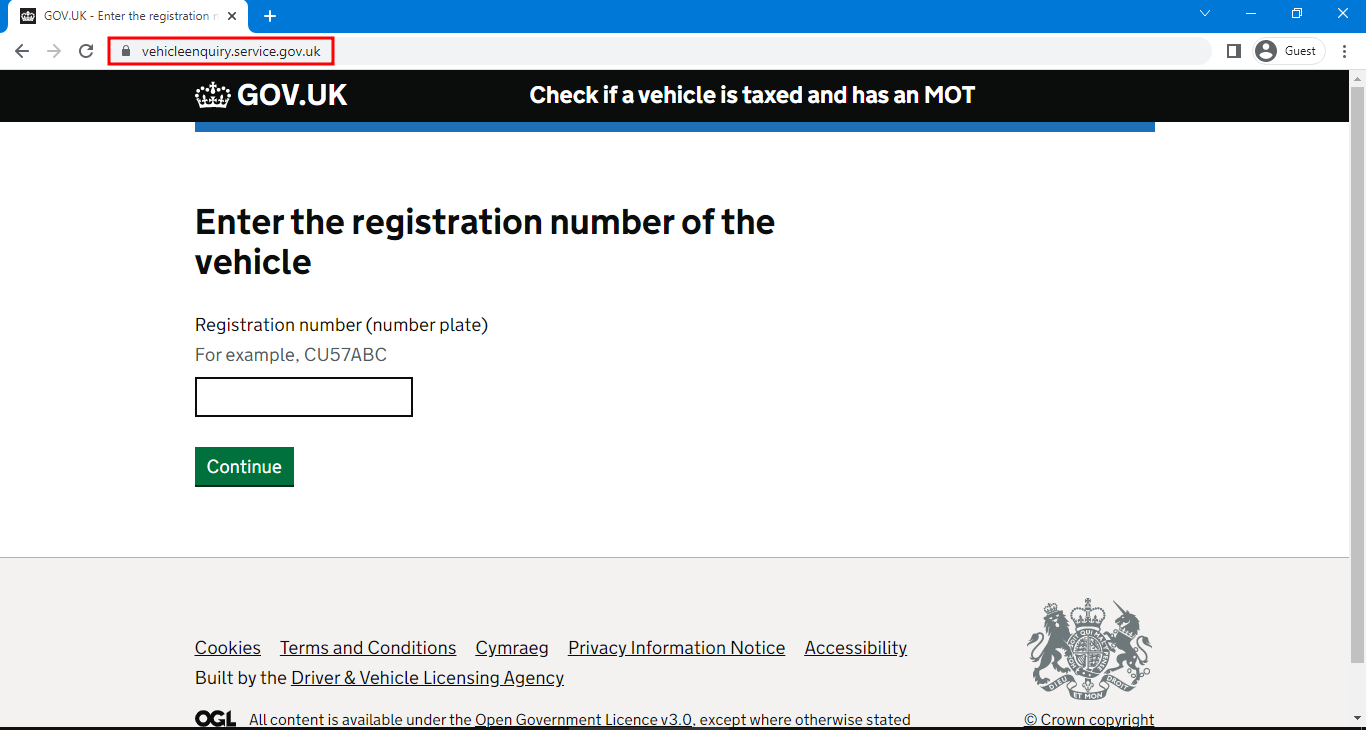
Do not enter sensitive data (e.g. contact information or credit card details) on insecure websites. To check if a website is secure, look at the address bar of the browser. The web address should begin with https://.
Use common sense when shopping online. If prices look too good to be true, proceed with caution!
Working Away From Your Usual Location
When away from home or your usual workplace, do not connect to public wi-fi networks. These networks are usually unsecured and do not require a password to be accessed. Instead, use a VPN (virtual private network). A VPN provides an extra layer of security by hiding your IP address and sending/receiving data through an encrypted "tunnel", so you can browse the Internet securely and anonymously. Consider choosing a service such as NordVPN.
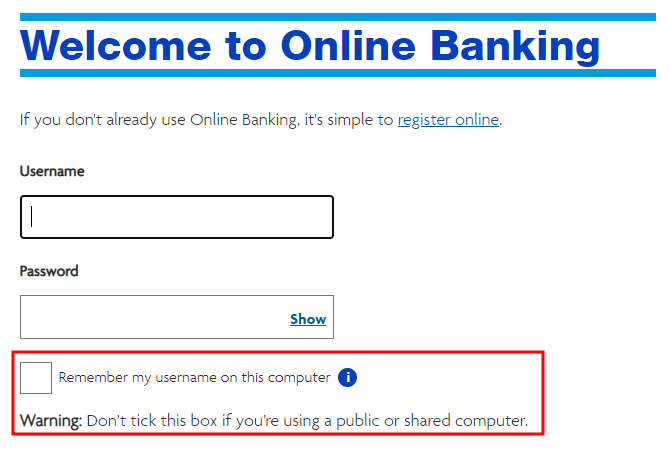
If you are accessing your accounts on a public computer, do not leave the computer unattended and always log out when you finish your session. Some websites can save your username or email address to make logging in faster - do not check this box if using a public or shared computer. Below is an example of a warning on an online banking site:
8. Ensure That Your Website is Secure
If you manage your own website, install an SSL (Secure Sockets Layer) certificate on your website. When a website has an SSL certificate enabled, the web address will begin with https:// rather than http://, and the browser may also display a padlock icon in the address bar. A secure website builds trust and reassures your customers that their data is safe on your website.
Most website builders provide an SSL certificate for free, so you would not normally have to worry about this. However, if you are using WordPress or another content management system that does not provide one, you can obtain a free SSL certificate from Let's Encrypt or purchase one from your domain provider.
Additional Tasks for WordPress Users
Make sure to update your plugins, themes and core WordPress files often (we recommend checking once a week). Updating your WordPress site helps to keep it protected against security threats and vulnerabilities. Read our handy guide on how to update your WordPress website the right way.
9. Monitor Your Login Activity
Perhaps a colleague has told you that they received an email or invoice from you that you were totally unaware of! How would you know if someone has tried to gain access to one of your accounts?
Many platforms include a feature that lets you track any suspicious behaviour; here is an example. If you are using Microsoft, you can go into My Microsoft account > Security > View my activity (below "Sign-in activity"). I recently tried this and was shocked to find out how many times someone had tried to gain unauthorised access to my account, but fortunately, none of the suspicious logins were successful.
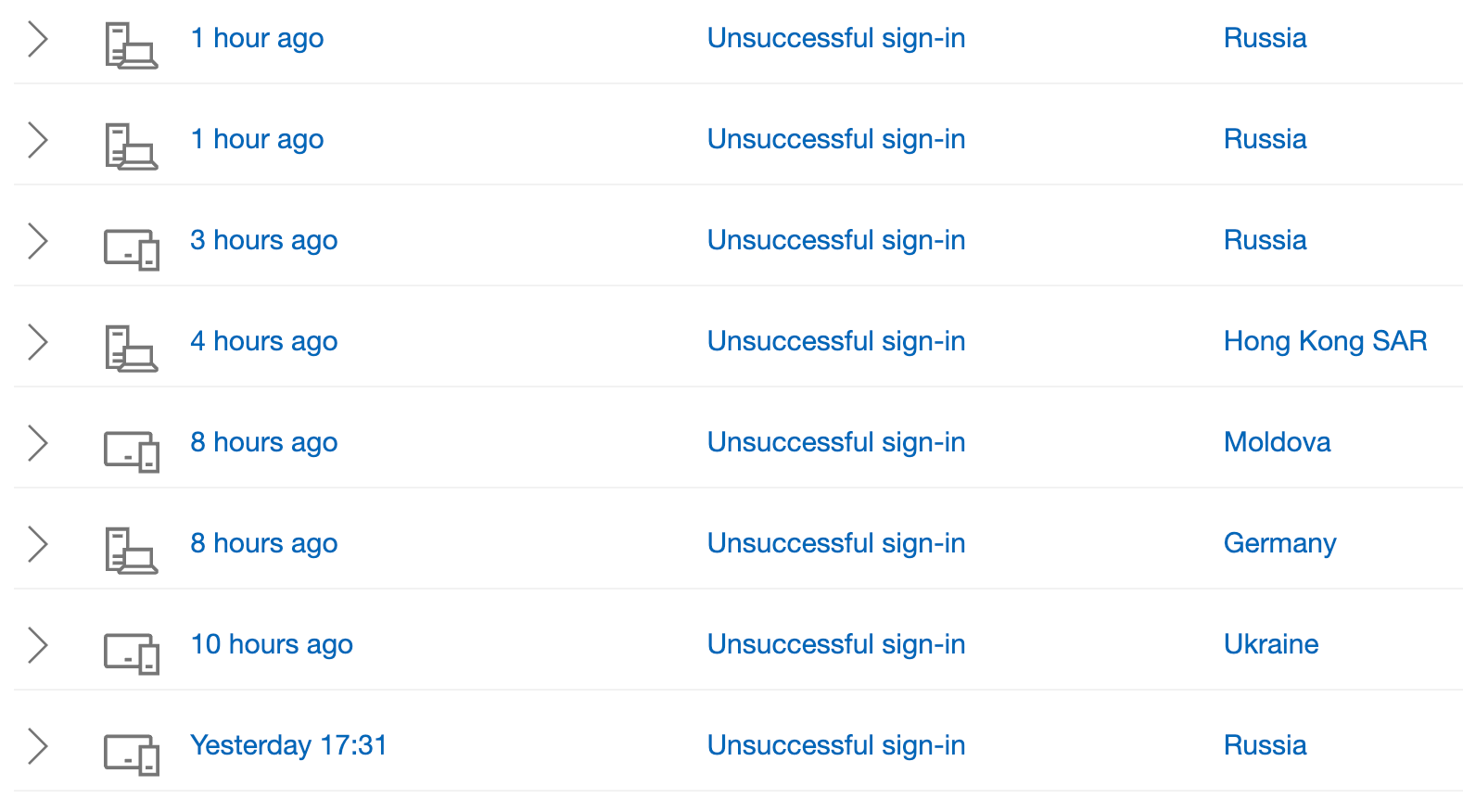
It's recommended to add additional email addresses or phone numbers to your Microsoft account. If Microsoft detects a suspicious (and successful) login on your account, you would receive an email notification or text with instructions on how to proceed. Changing your password would usually be the first thing to do. However, if you do receive such a notification, please ensure that it is genuinely from Microsoft - we have known scammers to spoof these "Unusual sign-in activity" emails too, as described earlier in this article.
If you do not use Microsoft, please check within your software to find out which security measures are in place for tracking sign-in activity.
10. Exercise Caution When Using Video Conferencing
Since the COVID-19 pandemic, the popularity of video conferencing tools such as Zoom, Google Meet and Microsoft Teams has increased significantly. This in turn has unfortunately led to a rise in cyber security issues. One such issue is "Zoombombing", where a Zoom meeting is gatecrashed by uninvited attendees.
Here are a few tips to keep your online meeting safe from intruders and other risks:
- Do not publish the meeting link publicly. Create a page on an events platform such as Eventbrite, so that attendees can register their interest beforehand. You can then vet the list of attendees and choose whom to share the link with.
- Disable the "join before host" option. Allow attendees to wait in the Waiting Room before admitting them to the meeting.
- Restrict sreen sharing to the host only.
- When screen sharing, close all windows or tabs apart from the one that you intend to share.
- Only record the meeting if it is absolutely necessary to do so. Inform all attendees that you will be recording it.
- Do not share personal information via the video conferencing platform.
- Consider using headphones if you are to make the call in a non-private space.
- Keep your video conferencing software up to date.
11. Stay Informed About Cyber Security Issues
There are many resources available online to help you stay up to date with the latest cyber security issues and tools to reduce your cyber risk. Here are a few to get you started:
12. Get Cyber Essentials Certified
Last, but not least, we recommend getting Cyber Essentials Certified. Cyber Essentials is a government-backed scheme which was developed in response to the growing problem of cyber crime. Getting certified demonstrates your commitment to cyber security best practices and gives you peace of mind that your organisation is protected from the most common cyber threats. The certification is available at two levels (Cyber Essentials and Cyber Essentials Plus). Once you have received the certification, you will receive a badge to be displayed on your website and other documents.
Our partners, The GDPR Compliance Consultancy, can help you through the process of getting certified with ease.


